What is a BYOD policy? An expert guide to bring your own device

Director of IT

Tags
Share
Personal devices are the cornerstone of most modern working environments. They’re not just a cost-effective way to kit up your workforce—they can significantly boost productivity and employee satisfaction, too.
Despite these compelling benefits, using personal devices can come at a price. Without the right security protocols and policies in place, you could inadvertently open your business up to a slew of security risks. This could result in lost data, hefty GDPR fines, and reputational damage.
That’s why it’s crucial to support your personal device usage with a robust bring your own device (BYOD) policy.
In this guide, we’ll walk you through a clear BYOD definition, detail the pros and cons of BYOD, and provide tips for implementing a BYOD policy.
Let’s get started.
What is BYOD?
BYOD, or “bring your own device,” is the practice of using a personal device for work purposes. Through devices like their own laptops or mobile devices, your employees can access the critical business applications and data needed to complete their day-to-day tasks—either on-premises or off-premises.
It’s important to note that while the devices belong to your employees, any business-related resources, applications, and data belong to your organisation.
When should you adopt BYOD?
There’s no one catalyst for introducing BYOD. Whether you adopt this practice or not depends on your unique business needs and employee preferences.
That being said, remote or hybrid working policies are often a key trigger.
In the UK, employees spend an average of one and a half days per week working from home. Naturally, these employees need readily available devices to help them complete their work and communicate with colleagues.
While you could purchase, set up, and ship company-owned devices to your entire remote workforce, this may become expensive over time. So, in this instance, BYOD is a faster, more cost-effective alternative.
If you find your employees are already using their personal devices to answer messages for work-related tasks anyway, you might already be a step ahead in implementing BYOD.
Devices at work vs. devices for work
Speaking of using personal devices, there are some important differences between devices at work and devices for work.
Devices for work are personal and/or business-owned devices authorised for work purposes.
Devices at work, on the other hand, are personal devices that employees use for work purposes without authorisation—they’re simply being used at work. For example, one of your salespeople may send a quick email to a prospect on their personal smartphone while in the breakroom.
While this isn’t a cause for immediate panic, repeated instances of this behaviour can pose a security risk to your business and its data—particularly if your IT teams aren’t aware.
This is because devices at work often don’t have any business-grade security controls or monitoring in place. Therefore, you have no choice but to trust that your employees know how to keep sensitive information safe.
And often, they don’t. That’s why it’s essential to have a robust BYOD policy.
What is a BYOD policy?
A bring your own device policy is a set of rules that define expectations, limitations, and responsibilities surrounding personal device usage.
In most organisations, senior IT leaders create these policies, as they focus heavily on security and data compliance best practices.
How does a BYOD policy work?
A BYOD policy outlines terms for IT departments, employers, and employees. When onboarding or offboarding a new employee or device, your organisation must follow this policy and enact its terms.
What does a BYOD policy include?
BYOD policies will look different for every business, but universally you can expect them to include information on device usage, security measures, privacy, IT support, and role-based responsibilities.
As well as written guidelines, these policies usually contain details about technical controls to help enforce the overall policy. We’ll cover this in more detail in just a bit.
Benefits of a BYOD policy
Now that you’re familiar with what a BYOD policy is, let’s outline the advantages of having one:
It supports remote and hybrid working policies
If given the choice, 43% of UK workers would like to work from home at least some of the time.
To meet these employee expectations, it’s important to create a working environment that facilitates remote work. With a good BYOD policy, you can empower your employees to use their own devices anywhere—whether it’s at home or in a local coffee shop.
It boosts employee productivity
Leading on from this, a BYOD-supported remote working environment can also improve team efficiency because it reduces the need for employees to constantly switch between logons and devices.
It also helps to have a BYOD-friendly collaboration platform. A solution like Dialpad Connect enables better employee collaboration and communication across your distributed workforce by letting team members make phone calls, have video chats, and send direct messages all from a single app:
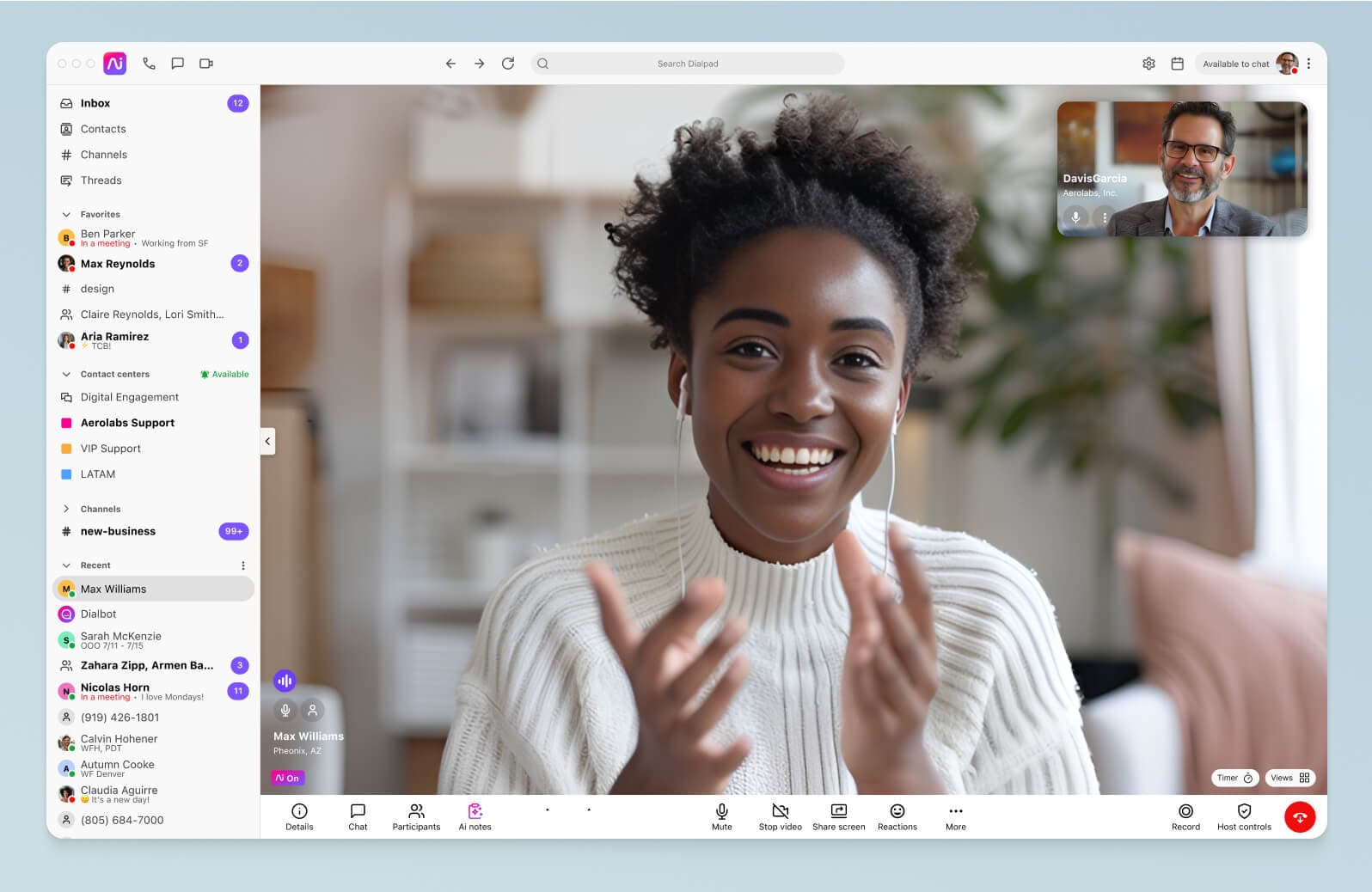
The result? Higher productivity rates and better ROI.
Dialpad tip:
With Dialpad, your sales and customer services teams can also easily forward a landline to a mobile. That way, you can easily route a call to a colleague working on a personal device either on-premises or off-premises.
It reduces device-related costs
Supplying company-owned hardware can cost a pretty penny or two, especially if you’re in the middle of a hiring boom
Permitting your employees to use their existing devices will significantly cut these upfront costs. You may also find that employees are more likely to treat their own devices with care, which can reduce repair costs further down the line.
It speeds up employee onboarding
Procuring, provisioning, and setting up devices isn’t just expensive—it takes time too. If you also have to ship these devices to your remote workforce, this timespan only increases. This can result in lengthy employee onboarding and lost productivity.
With a BYOD strategy, you can significantly decrease this set-up time—not to mention freeing up your IT department from a myriad of low-value software installation tasks.
BYOD policy challenges
But while having a BYOD policy offers major benefits, there are also some potential risks to be aware of—both during and after implementation.
Data security concerns
If your employees don’t follow security best practices, they could unknowingly share sensitive data, download malicious malware, or be susceptible to hackers.
These scenarios can result in data breaches, fines, and customer dissatisfaction—all of which cause significant damage to your business.
Decreased employee privacy
Your organisation doesn’t own your employees’ devices, but it does own the data and resources stored on them. Because of this, your IT teams will require access to parts of these devices. This may naturally result in privacy concerns.
To put your employees at ease—and respect their private information—your IT team will need to establish a strategy to separate personal and corporate data on personal devices.
Malware downloads
Once again, as BYOD devices are employee-owned, you can’t control the type of software or files your employees download.
Therefore, there’s a chance your employees could download malicious software, which puts your corporate data at risk.
Physical security risks
Finally, you must also consider the physical security risks associated with these devices.
Some employees may share their devices with family members or friends. If they don’t follow security best practices, this could result in your (and your customers’) sensitive information being seen or transmitted by unauthorised parties.
This security risk only multiplies if your employees frequently work from public spaces. In these environments, there’s always a chance that strangers may access sensitive data or steal the device. Whereas company-issued devices can be remotely shut down or wiped clean in cases of theft, this is typically harder to do with personal devices because IT teams don’t have the same level of control.
Examples of a BYOD policy: What should be in yours?
As we mentioned earlier, a BYOD policy should contain a list of rules, responsibilities, and technical controls to support personal device usage in your business.
Specifically, you’ll want to include the following in your policy:
Permitted devices
Beyond stating the kind of devices employees can use (such as laptops or tablets), specify what type of operating system they must have in place. This includes the version of that operating system. (Older operating systems will have fewer available software updates and may be more vulnerable to security threats.)
Acceptable use
How and when should employees use their personal devices for work? When shouldn’t they? Outline your exact BYOD terms.
In addition to this, detail expectations around data usage—specifically concerning storing, handling, and sending personal data.
Most acceptable use policies will reference regulatory best practices. For UK organisations, it’s important to align your efforts with GDPR and the Data Protection Act’s guidance.
Security practices
You should also reinforce your BYOD policy with stringent security measures, such as:
Using multi-factor and/or biometric authentication on devices as well as corporate applications
Creating strong passwords for all corporate accounts and applications
Encrypting data—and ensuring employees only transmit data via company-approved applications
Defining user permissions and making sure only the right individuals have access to sensitive data.
Dialpad tip:
Any workplace application you use (from your CRM to your business phone system) should adhere to these security practices, too. For peace of mind, choose software that offers enterprise-grade security.
Employer permissions and privacy
To improve the security of your BYOD devices—without interfering with your employees’ privacy—clearly define how you plan to separate employee and corporate data.
Detail the types of permissions and controls your IT department will retain, as well as how you aim to protect employee privacy.
IT support
What if your employees face unexpected technical or security problems with their devices? This may be as minor as an application not booting up or as serious as accidentally clicking on a phishing link in their corporate email account.
A BYOD policy must outline how employees can seek help in these instances. This will aid your overall security posture and allow your employees to troubleshoot and fix problems quickly.
Employee offboarding
When an employee leaves, you don’t want your sensitive corporate data to leave with them. To ensure your sensitive information remains safely in your hands, create a step-by-step protocol for removing data, revoking access, and unenrolling devices.
How to introduce a BYOD policy and what to consider
Once you establish your BYOD policy, what’s next? Like any change management initiative, it’s important to consider the rollout and messaging surrounding the implementation.
To give your BYOD policy the highest chance of success, here are some best practices to consider:
1. Run employee education sessions
Your BYOD policy will only be as effective as the employees who use it.
The question is: How can you ensure your employees follow your policy down to the fine print?
There’s no surefire way to enforce guidance. However, you can improve your chances by conducting regular security awareness and BYOD-specific training.
This will reduce the likelihood of data breaches, shadow IT usage, and poor security practices (such as weak passwords). It will also allow you to communicate expectations and responsibilities clearly, as well as offer your employees a chance to ask questions and raise concerns.
2. Embrace mobile device management (MDM)
Mobile device management uses role-based access protocols and data monitoring features to manage BYOD devices.
In essence, your IT department can keep a bird’s-eye view of all devices within your network, no matter where they’re working from. That’s essential for resolving security threats before they snowball into more serious issues.
MDM can also better divide personal and corporate data, in turn safeguarding employee privacy.
3. Enforce additional security tools
Beyond MDM and training, invest in additional security software—such as anti-malware and password management tools—and make them a requirement for all employees.
This will enhance security and reduce the likelihood of malicious malware infecting devices and impacting your business’ uptime.
4. Adopt secure productivity software
BYOD-friendly workplaces rely on secure productivity software. Without these tools, you’ll struggle to foster a truly collaborative and efficient workforce.
So, whether you’re looking for the best team communication tools or CRM platforms to support your BYOD practices, choose software with enterprise-grade security. Yes, native integrations, intuitively designed features, and built-in analytics are all important, but for BYOD environments, security should always be top of mind.
For example, a good communication platform will have built-in privacy settings like locked conference calls, regular penetration testing, and automatic redaction of sensitive information in call recordings and transcripts:

5. Back up your data regularly
Almost a third of all UK businesses experienced a cyberattack or data breach in 2023, according to a recent Cyber Security Breaches Survey.
There’s a strong chance your business could be part of this percentile. Even if it isn’t, it’s always better to hope for the best but prepare for the worst.
One crucial way to prepare for these events is through regular data backups. This way, if an employee loses their device or becomes the victim of a cybersecurity attack, you can reduce downtime, comply with data regulations, and rest easy knowing your data isn’t completely lost.
Dialpad tip:
To support these efforts, invest in software like Dialpad that automatically backups your BYOD device data.
Support your BYOD policies with a secure tech stack
With a strong BYOD policy, your business can boost productivity rates, save costs during employee onboarding, and facilitate flexible working practices.
But, in order to achieve these results, your policy should be supported with the right software.
Dialpad Connect, for example, works across a range of different devices and operating systems, making it truly BYOD-friendly. In addition to this, it can aid your security and data compliance efforts via built-in security features, Ai-backed encryption, and automatic data backup. Try it out for free!
See why remote workforces love Dialpad Connect
Try Dialpad for free with a 14-day trial, or take a self-guided interactive tour of the app first!








