
Tags
Share
If your business operates on a flexible, remote or hybrid model, you’ve probably realised supplying all the right tech to your employees can be tricky! Do you order new devices online and get them delivered? Or post out phones from your central office in Sydney over to Christchurch—or beyond?
It’s no surprise, then, that Bring Your Own Device (BYOD) policies are on the rise. Before you dive right in, however, keep in mind there’s a lot to consider when you start to implement a BYOD policy—and much of that burden will fall on the IT team.
In this guide, I’ll break down everything you (and your IT team!) need to know about BYOD policies—from their benefits and risks, to how to successfully implement one in a business or organisation.
What is a Bring Your Own Device (BYOD) policy?
Basically, a BYOD policy is the set of rules that governs how employees should (and should not) use their personal electronic devices, like laptops, smartphones, and tablets, in the workplace and for work purposes.
BYOD gives businesses a more budget-friendly alternative to purchasing and issuing work-specific devices for all their employees. Instead, it allows employees to access the company network, apps, and so on from their own devices, either on premises or remotely.
The advantages and disadvantages of adopting a bring your own device policy
As with any policy, there are pros and cons to BYOD. If you’re considering implementing a BYOD policy at work, here are the main advantages and disadvantages to consider.
Advantages of having a BYOD policy
Cost savings for the business
One of the biggest benefits of BYOD policies is the amount of money your company can save. You don’t need to spend anything on work devices for employees, and, since staff are using their own devices, you may find they also take better care of them. (It also means it’s no longer your responsibility to replace broken or stolen devices.)
Of course, one of the biggest considerations for BYOD is that your company will have to use software and applications that work across different operating systems and devices. When employees are using anything from iOS to Android to PC and Mac devices, your virtual phone system or communications platform, for example, would have to work across all of them.
Dialpad is BYOD-friendly, with its desktop and mobile app working across these systems. That means our customers can make phone calls, have video meetings, and send instant and SMS messages from their computers or mobile phones:
📚 Further reading:
That’s exactly what PagerDuty did—check out their story here. As one employee said, “Just day one, one of the apps that was provisioned was Dialpad… so I downloaded the app, logged in, and it was very straightforward—it basically worked like my iPhone”.
Faster onboarding
If your company is hiring or scaling quickly—especially if you’re talking about hybrid or remote work—it saves a lot of time to allow employees to use their own devices instead of shipping off equipment to every single person. Plus, they’ll already know how to use it!
Easier to keep software up to date
Making sure all of your employees have updated their laptops and work phones can be time-consuming. Rolling out company-wide hardware updates can be costly too. If employees are using their own smartphones and laptops for work, they’re more likely to keep on top of software updates and replace hardware when necessary.
More flexibility
Remote and hybrid working is here to stay. When you can use your own devices for work, you have far more flexibility around when and where you work. Employees can be as productive and as accessible as colleagues in the office, whether on a business trip or working from home.
📚 Further reading:
See how Kelly Winstrom, Director of IT at Andy Mohr Auto, moved over 1,000 employees to a cloud-based communications platform and allowed them to use a range of different devices.
Possible disadvantages of having a BYOD policy
You give up some employee privacy
Just as companies may be concerned about privacy when implementing a BYOD policy, employees may feel the same. Your company may wish to monitor your email or browsing history even more closely if you’re using a personal device, making the lines between your personal and professional life blurry.
It can make IT support more complicated
When everyone is using identical laptops and mobile devices, IT support is simple. Things like upgrades and maintenance can get more complicated when the IT department have to deal with individual pieces of equipment and operating systems. That being said, most companies issue different types of devices to employees anyway, depending on what they prefer (for example, employees can choose between Apple and PC computers), so this may not make that big of a difference.
Malware
On a related note, malware isn’t something that you can avoid completely, even if your company issues all work devices instead of going BYOD. Malware may be more of a problem for companies with BYOD policies—but if you have a good security training program for employees and a well laid-out policy, it might be less bad than you expect!
What should be part of a BYOD policy?
Now you know the pros and cons of BYOD policies, let’s look at what you should include in one beyond just “this is what’s okay and not okay for personal use.”
A robust communications platform
BYOD or not, you need to be sure that the employees in your company have a way of communicating with each other across different devices. Your business phone system or video conferencing software—or your unified communications platform, if you’ve streamlined everything into one tool—should be accessible on different types of devices.
For example, as I mentioned earlier, Dialpad works across iOS, Android, Mac, and PC. It allows employees to make phone calls, have video meetings, send instant and SMS messages, and more, all from the desktop or mobile app. All employees have to do is download the app…actually, they don’t have to do that either, since Dialpad is browser-based and works in web browsers too with full functionality:
🧠 What's keeping CIOs up at night?
We interviewed 12 CIOs across a range of industries like healthcare, law, and higher ed. Get the playbook to learn about their approaches to data security, hybrid work, and more!
Establishing company rights on the devices
BYOD and acceptable use policies can slide into tricky legal areas. Who owns the data on a device and the phone number attached to it? What happens when an employee leaves the company while still possessing company data on their BYOD device? If you’re putting a BYOD policy in place, chat with your lawyer before drawing it up. Always make it clear to employees where you and they stand from a legal perspective.
Device authentication
Putting in additional device authentication measures is a useful security policy for companies with BYOD policies. Sensitive data or not, implementing two-factor authentication (2FA) is now a common best practice to give employees that extra level of security. Regular re-authentication, such as asking your employees to input their password every few weeks and change their password on their personal devices every few months, are also good habits to build into your company policies.
Which devices are required or allowed
BYOD policies might remove limitations on what devices employees can use for work, but that doesn’t mean it should be a free-for-all. You may want to specify whether employees can use only certain generations of phones or laptop operating systems. (For instance, you may not want to devote IT support resources to supporting iPhones and iPads from 10 years ago.)
Disclosure of risks, liabilities, and disclaimers
BYOD policies need to be transparent and understandable to employees. Whether it’s legal disclaimers about company data or security measures and reminders, any company’s BYOD policy should have clear disclosures about the risks and liabilities associated with the policy.
Provisions
There are certain provisions you can put in place in your successful BYOD policy to ensure that things go smoothly.
Passwords
Mandate that all employees use strong passwords on their electronic devices, even for apps and websites that they don’t use for work purposes. Just make sure you’re not overloading them, and consider SSO (single sign on) services as a way to reduce the amount they need to remember.
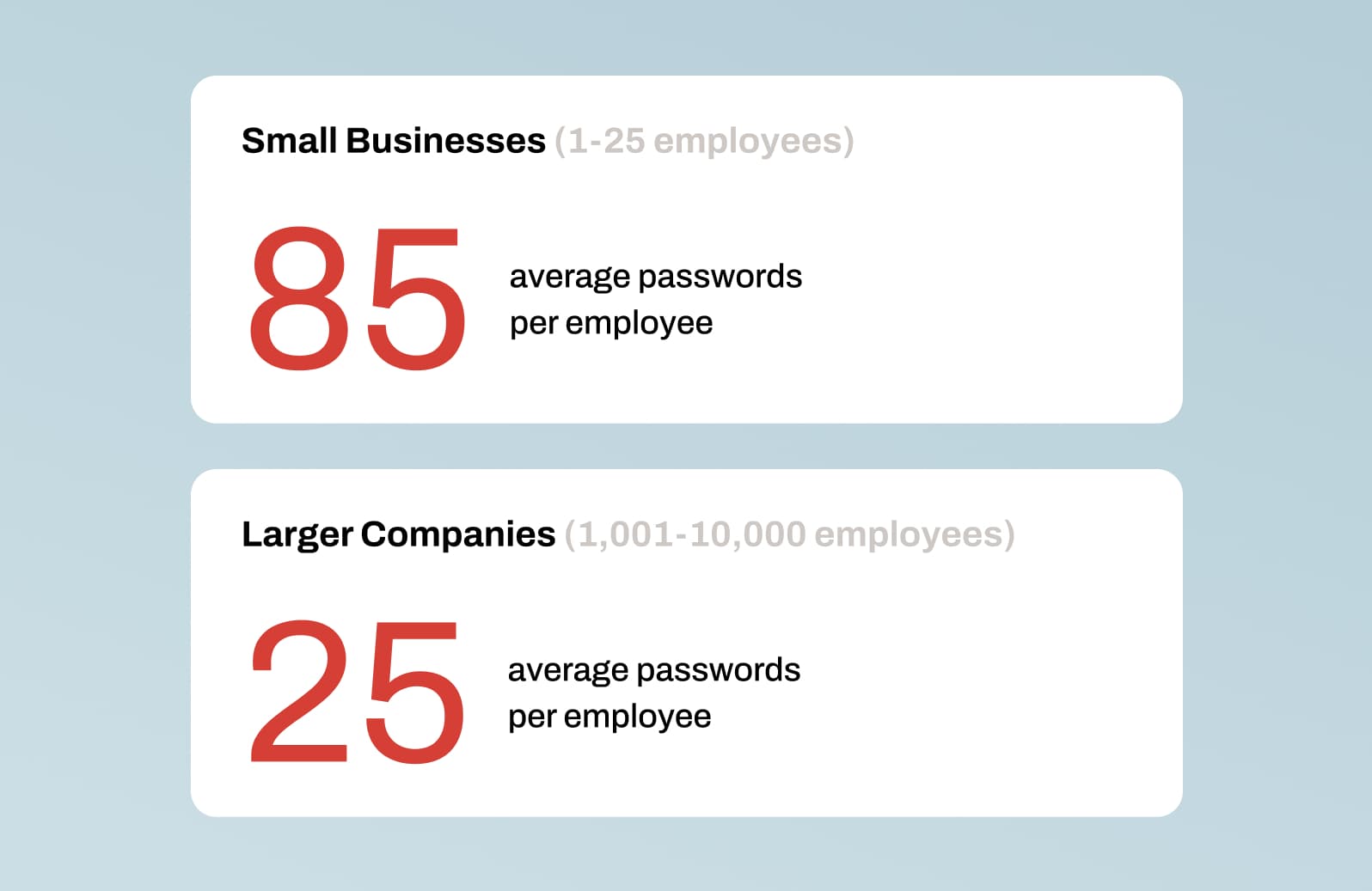
Fun fact: According to LastPass’s recent report, large enterprise companies actually have fewer passwords per employee on average:
Data transfer
Ensure that data is encrypted, password protected, and only being transferred across devices and apps that are approved by your company.
📱 Dialpad tip:
When implementing a BYOD program, use software that has enterprise-grade security and data encryption.
Privacy
Privacy is essential to both employers and employees. A successful BYOD policy should set out how privacy is being maintained for employees, as well as how company data will be protected.
Maintenance and support
BYOD policies should also let your employees know what kind of IT support they should expect for their personal devices. This might include specifying that devices be kept up to date, that only certain applications should be used for work or security purposes, and that IT departments will vet all new devices.
8 tips for reducing the security risk of your BYOD policy
Security is one of the biggest concerns for companies implementing a BYOD policy. Here are some steps you can put in place to ensure you and your employees’ devices are secure.
1. Have an employee off-boarding plan
BYOD policies get even more complicated when an employee leaves. When putting together your policy, don’t leave off-boarding out until it happens. Create an off-boarding plan that ensures sensitive information and data is removed from the device and the employee can no longer access the corporate network or data.
2. Use mobile device management (MDM)
Mobile device management, or MDM, is a strategy that you can employ to ensure mobile devices are being used securely by your employees. MDM is often delivered via networks, apps, or the cloud to secure data on mobile devices, segregate corporate data from personal data, and monitor and restrict mobile device use.
3. Use application readiness automation
Your MDM should also include application readiness automation to ensure devices are kept secure and lessen the burden on your IT departments. This might include automated compatibility tests and security patches for all BYOD devices.
4. Invest in anti-malware technology
If your staff are using their own devices, they may not have effective anti-malware technology installed to protect their devices’ vulnerabilities. Reduce the risk of malware and cybersecurity attacks by investing in anti-malware software that employees are required to install on any device they are using for work to ensure device security.
5. Strategise for device loss
Accidents happen and devices are lost and stolen. You can’t always stop this, but you can prepare for it. Have a plan in place for when (not if)a device gets lost. This might include installing software on employees’ devices that can wipe sensitive data should the device be lost or stolen.
6. Conduct regular data backups
If your device is lost or stolen, or company information is compromised or wiped accidentally, the last thing you want to worry about is losing the data entirely. Regular data backups are essential to any company’s BYOD program.
7. Create a clear reimbursement policy
Your company may have a legal requirement to reimburse you for expenses incurred through work. If your company has a BYOD policy, this could include reimbursement for an employee’s mobile data plan or even covering the cost or lost or stolen devices. If you’re putting together a BYOD program, consider what you might need to reimburse employees for and how you will manage this.
8. Provide extensive BYOD policy training
You can put in all the secure measures and mandates you like, but employees will use their personal devices as they please most of the time. The best way to prevent cybersecurity attacks or data breaches is to give your staff extensive training. Clearly set out what is acceptable use, and what possible risks they may encounter. Training will give staff the knowledge and tools they need to use their BYOD devices efficiently and securely.
📱 Dialpad tip:
There’s also penetration testing (or a PenTest), which is essentially simulating a cyber attack. PenTesting can be expensive and is generally reserved for validating customer-facing systems (if you’re a SaaS company, for instance) and not endpoint devices as part of BYOD. But, it’s still something to be aware of.
Create a flexible working environment with an effective BYOD policy
An effective BYOD policy can save your company money, improve productivity, allow for greater flexibility, and increase employee satisfaction.
One key thing to remember is to make sure your software service providers are compatible with your policies in terms of security and accessibility.
If you need a good communications platform, Dialpad works on a range of devices and operating systems, making it ideal for companies with a BYOD policy that don’t want to worry about purchasing and installing expensive and complicated hardware, software, or infrastructure. See how it works for yourself.
Need a communications platform that's designed to support BYOD policies?
Book a product tour of Dialpad's unified communications platform to see how it empowers distributed teams to make phone calls, have video meetings, and send instant + SMS/MMS messages—all from the same place!









